This is a follow-up to a previous post about how to hide API keys in Python. I received a good question on YouTube:
If I have my code deployed on a server from a repository, will hiding my API key using this method so that it is not visible in the repo affect anything?
Good point. And the quick answer is no, you should not use a .env file to store API keys when deploying to a server, because they’s a chance that file could be seen by others, especially if you’re deploying from GitHub, for example. But fortunately there are a couple of alternatives that can keep your keys secret:
Option 1: Set variables directly on the server
In the server’s terminal, use the export command to set environment variables, like this:
$ export API_KEY="my-key"It’s easy but the disadvantage is that it’s one-time only – the variable will disappear when the server is rebooted. To make it persistent, add the variable to a shell startup file like .bashrc (on most Linux servers) by running this terminal command:
$ echo 'export API_KEY="my-key"' >> ~/.bashrcTo make this take effect, either reboot the server or run the .bashrc file by running this terminal command:
$ source ~/.bashrcOption 2: Use your host’s variables feature
This is my recommended method because hopefully your hosting platform has a secure way of storing API keys and keeping them secret. It varies depending on host, so here are instructions for some popular ones:
- AWS EC2: You can set environment variables in the user data script when launching an instance, or use AWS Systems Manager Parameter Store or AWS Secrets Manager for more sensitive data.
- AWS Lambda: You can set environment variables in the AWS Lambda console, AWS CLI, or AWS SDKs.
- Docker: You can set environment variables using the
-eflag when starting a container, or by including theENVcommand in your Dockerfile. - Heroku: You can set environment variables (config vars) via the Heroku Dashboard in the app’s “Settings” tab. You can also use the Heroku CLI:
heroku config:set API_KEY=my-key --app my-app - Kubernetes: You can set environment variables in your pod’s YAML configuration file.
- Netlify: You can set environment variables in the Netlify Dashboard in the app’s “Build & deploy” settings.
- Vercel: You can set environment variables in the Vercel Dashboard in the app’s “Settings” -> “Environment Variables”.
Example: Environment variables on Heroku
As an example, here’s the step-by-step process for setting environment variables (they call them “config vars”) on Heroku.
- Go to your app’s “Settings” page.
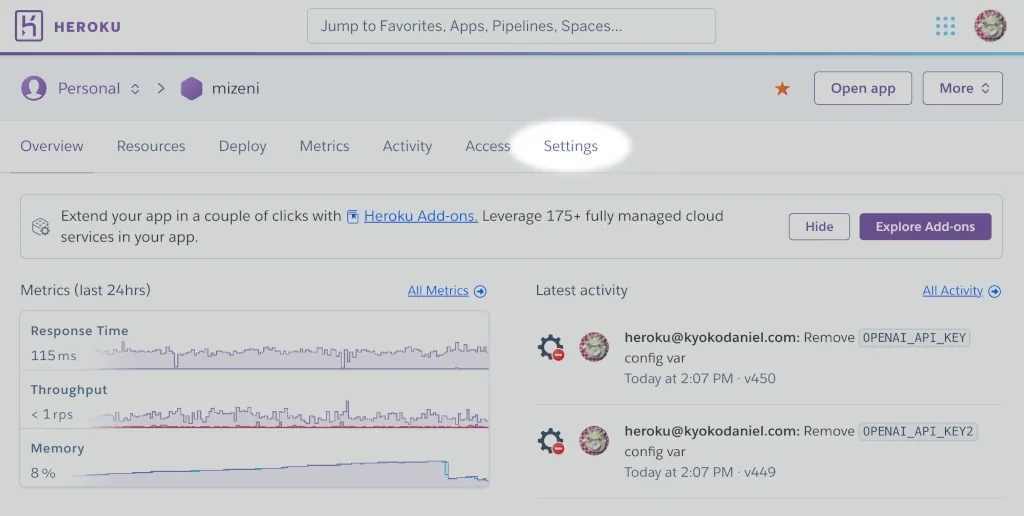
2. Click the “Reveal Config Vars” button.
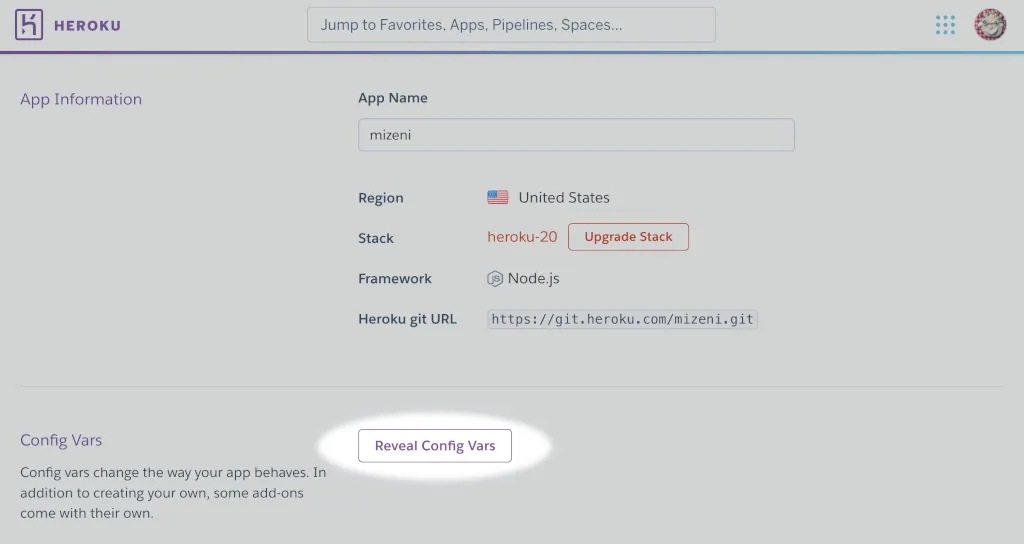
3. Add keys (names) and values for any API keys you want to store.
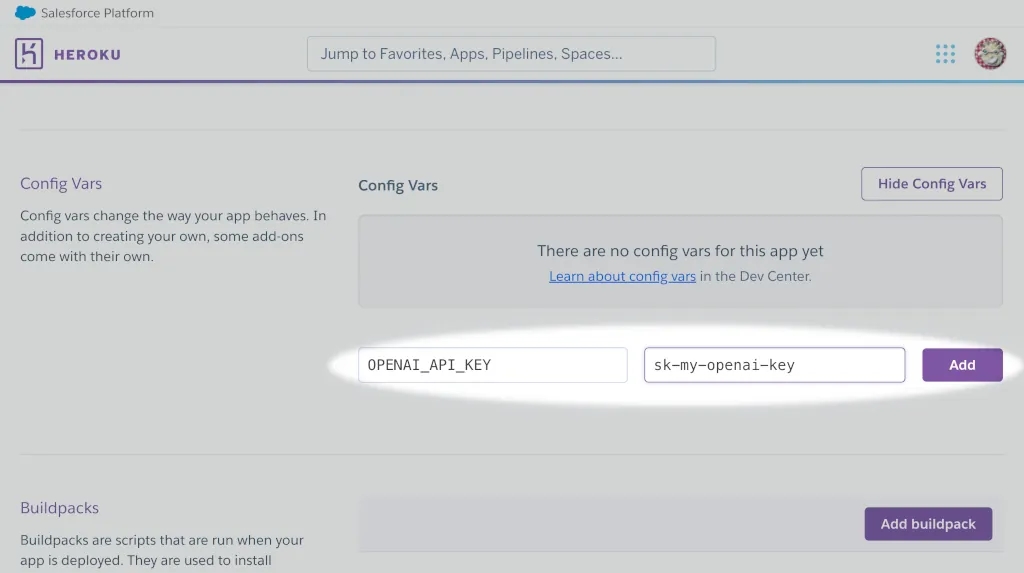
Access the environment variables in your code
Whichever method you use to store the environment variables, you can now access them with Python using the getenv() method in the built-in os module (i.e. no installation necessary).
Here’s an example using an OpenAI API key, assuming that the key’s variable name is OPENAI_API_KEY:
import os
import openai
openai.api_key = os.getenv("OPENAI_API_KEY")One more thing…
If you have a .env file for local development and you use Git, make sure you add .env to your .gitignore file to prevent it being accidentally committed to your Git repository, especially if you have a public repository on GitHub, etc.
If you ever commit API keys to a repository, even if you delete them later, they may still be accessible in the repository’s history. If this happens, assume those keys are now public. Delete and recreate them as soon as possible.

Leave a comment